Author: Dennis Tkacs
Not a day goes by without mention of a new cybersecurity incident, the hack of a prominent organization’s website, a new security threat, or an attack that compromises consumer financial information. US based retailers Target and Home Depot are recent examples of companies befallen by cyber-attacks.
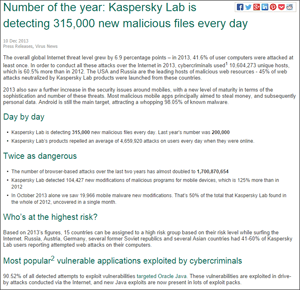 The number of malicious files is staggering; Kaspersky Labs, a leading security software firm, reports detecting 315,000 new malicious files every day.
The number of malicious files is staggering; Kaspersky Labs, a leading security software firm, reports detecting 315,000 new malicious files every day.
As damaging as cyber-attacks against personal and business systems can be, these attacks can be even more devastating if directed at critical infrastructure. Critical infrastructure systems, including power generation and transmission, refining, manufacturing, and others, use control systems that largely consist of commercial-off-the-shelf computing technology.
The use of common operating systems and technologies in this industry means these systems can be at risk for cyber-attack and compromise, much like our home computers, if appropriate security controls are not in place and up to date. These same Trojans (viruses and worms that can impact a personal or business computer) can also attack an operator console or other component of the control system, shutting down a process, tripping a unit, or causing some other unintended consequence.
 The most prevalent threats facing industrial systems are not external threats, but rather come from unintentional internal events like an employee using an infected memory stick on a production system or a supplier using infected computers to provide maintenance or service a system. While unintentional internal threats are most prevalent, it is important to recognize that threats can emanate from a variety of sources.
The most prevalent threats facing industrial systems are not external threats, but rather come from unintentional internal events like an employee using an infected memory stick on a production system or a supplier using infected computers to provide maintenance or service a system. While unintentional internal threats are most prevalent, it is important to recognize that threats can emanate from a variety of sources.
Threats can be categorized as follows:
Unintentional hackers – this group of hackers do not realize they are impacting control systems and infrastructure. Typically these attacks are unintentional in nature, non-malicious and accidental. Other accidental hacks may include granting access to system resources to someone unauthorized to make changes that result in loss of production.
Recreational hackers – these individuals see infiltrating a computer system as a game of sorts. They may vandalize a website but the damage they cause is relatively minor. Also included in this tier is the disgruntled employee looking to inflict harm on their employer by compromising systems and production reliability. While a real threat, these are typically unsophisticated in nature and can be prevented with the right access controls.
Organized crime – this tier is motivated by financial gain. Attacks can be directed at individual or commercial interests.
Political hackers – unlike the third tier these groups are not interested in making a profit. Political hackers are interested in making a statement and/or disrupting a business or government entity with which they disagree.
The bottom line is that critical infrastructure is vulnerable to outside cyber threats and companies need to establish strong security controls in order to protect these assets. Suppliers such as Emerson can provide assistance to companies as they wade through the complexities of combating cyber-attacks while trying to meet standards put forth by governmental agencies such as the Federal Energy Regulatory Commission (FERC) and the North American Electric Reliability Corporation (NERC).
In my next post, I’ll discuss evolving Critical Infrastructure Protection (CIP) standards and their potential impact on a variety of industries. Going forward I’ll also address what can be done by industrial users to address cybersecurity threats.
From Jim: You can connect and interact with other power industry professionals in the Power track of the Emerson Exchange 365 community.




